Integration
U-alarm is not only a standalone solution but can be used in an integrated system as well. Each article contains valuable information about the required settings in U-alarm as well as in the corresponding third-party software.
General concept
Components
The integration has 3 components:
U-alarm
Third party application (preferably a VMS)
a Connector
Note: In this document the Third party application is often referred to as VMS, however it can be any software with similar capabilities.
Topology
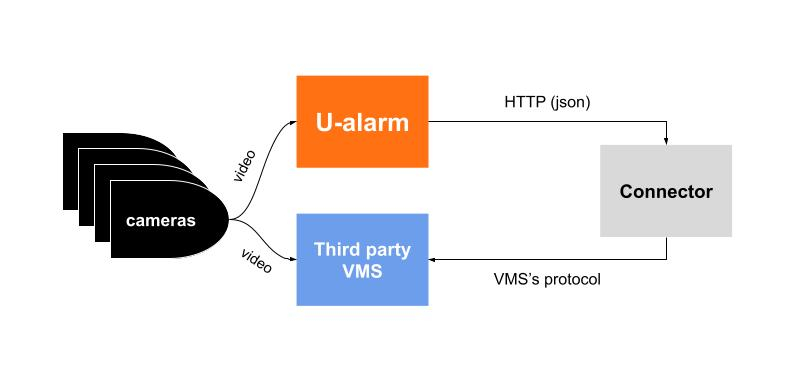
U-alarm
- Receives video streams from cameras.
- Detects incidents.
- Notifies the operator on its user interface.
- Sends Event messages with metadata to an external API via HTTP.
VMS
- Receives good quality video streams from cameras.
- Stores videoProvides user interface for operators including incident management.
- Has an interface to receive real time notifications (alarms/events) from external sources.
Connector
- Dedicated to a specific VMS.
- Usually running on the same machine as the VMS.
- Associates streams registered in U-alarm with streams registered in the VMS (easier if the VMS provides a unique identifier for each camera).
- Receives Event messages from U-alarm.
- Converts U-alarm Events to a message which is readable by the VMS.
Capabilities
Capabilities are determined by both U-alarm and the VMS. The following information is available in the U-alarm Event’s metadata:
- the incident’s type (crowd detection, intrusion)
- the timestamp of the incident
- camera identifier(s)
- the detections’ coordinates in the camera frame
- confidence value - events with lower confidence can be filtered in order to decrease false positive alarms
(Learn more about the metadata for your Custom Integration...)
This information is translated by the Connector component. The capabilities of the VMS may limit the forwarded information and the overall end user experience.
Example scenario
Installation
- U-alarm is installed on an NVidia Jetson TX2 box.
- The VMS is installed on a Windows server.
- The Connector is installed on the same machine.
- Both machines are on the same local network with fixed IP addresses.
Configuration
VMS
The VMS is configured according to its own documentation with the following requirements:
- Observed Cameras must be registered in both U-alarm and in the VMS. The VMS may use the primary stream of the cameras with higher resolution and FPS compared to U-alarm. A unique identifier should be memorized for each registered camera. The identifiers will be used in U-alarm configuration.
- Access credentials for the connector.
- All other settings in order to receive external events.
Connector
Connector must have the following information:
- Access credentials for the VMS.
- An unused port for its service.
- The (network) location of the VMS interface.
U-alarm
U-alarm is configured along its own documentation with the following exceptions:
- Observed Cameras must be registered in both U-alarm and in the VMS. U-alarm often uses a secondary stream of the same camera with lower resolution and FPS.
- Cameras’ Technical names must be set. Each technical name should be unique and should match the unique identifier of the same camera in the VMS.
- The network address of the Connector (host, port) must be set in the Alarm configuration.
Workflow
In this example let’s say we configured intrusion detection in U-alarm.
- The intruder enters an observed area
- The camera stream is sent to U-alarm
- U-alarm detects the intruder and immediately sends an Event to the Connector.
- The Connector converts the incoming Event and sends it to the VMS.
- The VMS triggers an alarm and notifies the operator.
Implementations
Milestone XProtect
Milestone Xprotect is one of the most popular Video Management Systems. U-alarm is able to send Alarms to this system so you can manage incidents in your well known platform.
Alarms via E-mail
U-alarm can be configured to send alarms via e-mail. This enables you to use U-alarm in conjunction with e-mail notifications, or omit the use of U-alarm altogether. The service can be set up to be used by either human beings or automated systems.
Custom Integration
This guide will aid developers in order to receive and process Alarms triggered U-alarm in their custom solution.
