Zone Crossing
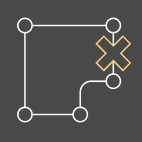
You can use Zone Crossing to notify you if an object (a person or any one of the 8 vehicle classes) enters an unauthorised area from a certain direction. Detections from any other type of movement will be ignored and will not generate alarm notifications. This type of alarm is most useful if you would like to prevent access to an area from only certain directions but allow authorised employees leaving the office, for instance.
The zones and the direction from which entry should trigger alarms are configured via regions of interest, by using the Camera Editor.
| Object movement | Will trigger alarms? |
|---|---|
| An object leaves the Target area (in any direction). | X |
| An object, coming from outside both areas, enters the Target area. | X |
| An object is is detected inside the Target area. | X |
| An object, coming from the Source area, enters the Target area. | ✓ |
- Core technology: full body and vehicle detection with object tracking.
- A camera with a minimum of 6 FPS is required!
- Will use 2 analysis slots (due to the tracking feature) by default.
- Compatible with fixed, PTZ, and thermal cameras.
- Areas of interest must be defined.
- Send data to third-party software.
New Zone Crossing
- Choose Zone Crossing by clicking on its box. Fill in the form, as follows:
- Name: A readable name of this alarm. This name will appear in the Events view and in all notifications.
- Armed: The alarm can be deactivated here. Armed by default.
- Schedule (optional): You can associate one of your previously defined Schedules with this alarm.
- Add Camera: Select a camera from the list.
NOTE: Cameras below 6 FPS will not show up on the list of cameras for Zone Crossing!
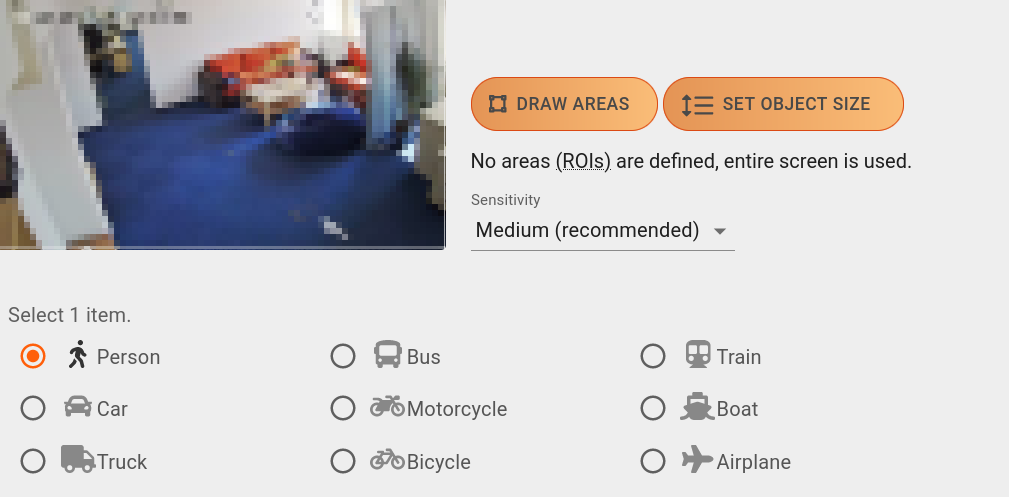
- Draw Areas (ROI) (mandatory): Since this type of alarm aims to detect unauthorised entry into given areas, ROI drawing is necessary. The following types of ROI are available:
- Source (at least one): An alarm will be triggered if an object moves from this area into a Target ROI. Otherwise, objects inside a Source ROI will not trigger alarms under any circumstances.
- Target (at least one): An alarm will be triggered if an object moves from a Source ROI into a this area. If an object enters from anywhere else (including the Target ROI itself), no alarms will be triggered.
- Exclude (optional): This ROI corresponds to the Negative ROI of other alarm types - no object inside this area will trigger an alarm. Exclude ROI take precedence over the other two types, if they overlap.
You can draw multiple numbers of each ROI type - at least one Source and one Target is necessary.

Set object size (optional): If you have a good idea of what pixel range the detected objects would fall into, you can customise the minimum and maximum height size of detections, in pixels, here. This would ensure that only objects that fit into that range would get detected, resulting in a further decrease in the number of false alarms.
Move the the arrows by clicking and dragging them to help you determine the optimal values. Adjust the slider's endpoints on the bottom part of the screen to set the minimum / maximum values. Click Set sizes to save your changes, or Discard to cancel them.
NOTE: Take care that any object below or above the set range will NOT be detected, possibly resulting in missing incidents. It is good practice to set the minimum size slightly below, and the maximum size slightly above the desired amount.
For example: If using Ultinous AI Suite with a combination of radar and PTZ cameras, setting custom object sizes would result in detections only if the radar have detected movement - since setting the proper minimum size would rule out random noise causing false detections.
Sensitivity : The sensitivity of the detector can be fine tuned here. Lowering the sensitivity causes less false detections but decreases accuracy. Increasing it results in more alarms but may cause more false detections as well. The default sensitivity is Medium.
Object types: Choose a single object type from this list (Person by default).
Enable HTTP webhook (optional):
Enables / disables event sending: Use this feature to send triggered events to a third-party software with an optional snapshot image of the incident attached. Sends a HTTP POST request to the URL set below, with a content type of
application/json. Read on to learn about the schema formatting. It is also possible to include an End of Event timestamp, which triggers if 5 seconds have passed without incidents after the initial event that triggered the HTTP message. End of Event occurs once the incident is over.The following information should be provided by the third-party software's administrator:
- Target URL: The location of the API.
- Header key and value: Key and value of custom HTTP header. Click the Add button to add more Keys. To delete a Key, press the Trash icon next to it.
- Trust all certificates: If enabled, HTTPS certification errors will be ignored.
NOTE: Custom CA certificates can be uploaded in the Trusted Certificates setting.
- Enable snapshot attach: Off by default. If enabled, it fills in the
snapshotfield of the http message schema in base64 encoded format. - Send end of event: Enables / disables End of Event sending. Note that the Cooldown setting of the Alarm has no effect on this.
Send Test Event: To test your integration, click the Send Test Event button once the HTTP webhook settings are set.End of Event records are sent as part of HTTP messages. They are not available in Milestone XProtect or in e-mail format.
Email notification configuration (optional):
This feature allows you to send alarms via e-mail to designated recipients.
IMPORTANT: Make sure that sender e-mail settings are already set! See the Sender configuration section for instructions.
- Enable snapshot attach: Off by default, sends a snapshot of the event in
.jpegformat. See the Snapshot part of the guide for its properties.
- Enable snapshot attach: Off by default, sends a snapshot of the event in
Enable Genetec Security Center integration (optional): Ticking this button to set a custom event ID is one of the steps necessary for sending alarms to Genetec Security Center. See the Genetec integration guide for detailed instructions.
Click the Submit button to save your settings.